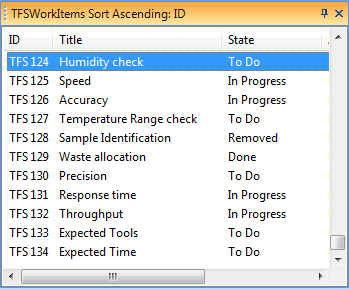
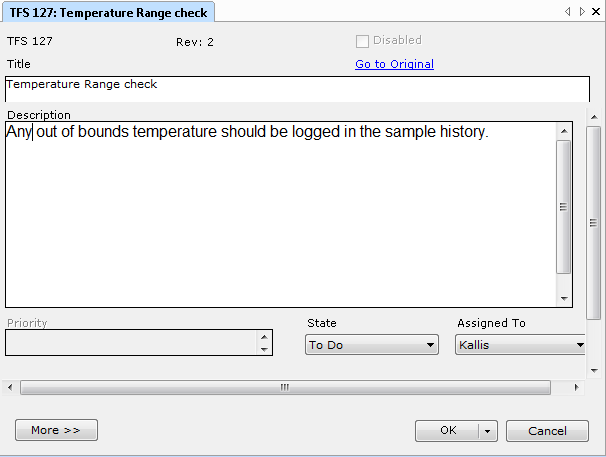
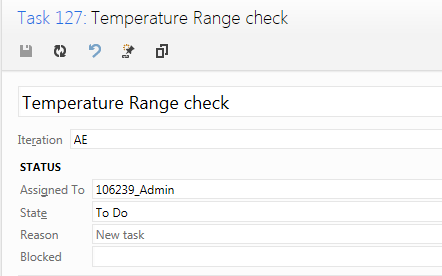
Start your road to efficient medical device documentation here!
{fastsocialshare}
You spend too much time and money on documentation.
Agreed?
Good.
So what is your plan?
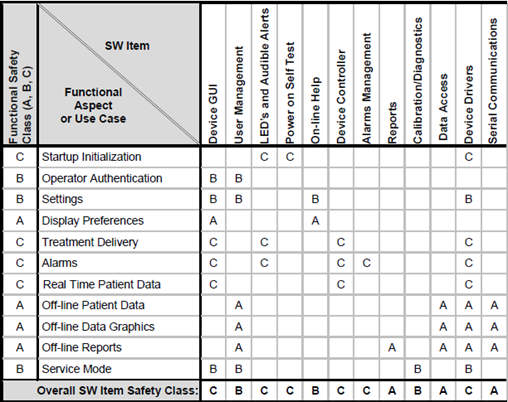
The regulations of the medical device industry require us to produce a pretty hefty chunk of documentation to show that the device is safe and efficient. If the documentation is not compliant, then it does not matter how safe, secure and performant the device itself it. Therefore, the documentation aspect that receives the largest share of attention is compliance. The most common path to a compliant stack of documents is to throw heaps of man-hours at the problem. Quantity seems to be the weapon of choice in many firms.
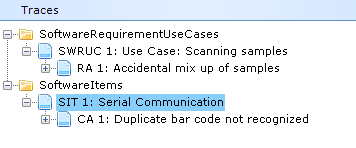
As a consequence, a large number of people get involved in the documentation creation and maintenance, especially people residing in the R&D part of the organization as most companies do not have Document Officers or documentation experts in their organization.
However, engineers and scientists are not necessarily the best writers (And they probably have no ambition to be.) Staff who are necessary for other tasks struggle to find the time to write these documents, and so the documents they do produce may be of lower quality than their usual work.
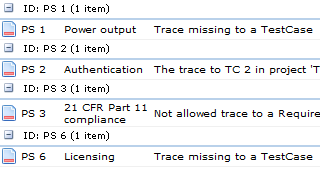
The effect on these people is often a suffocating feeling of inefficiency and frustration of spending an un-proportionally large part of the working day on menial documentation tasks, deciphering SOP:S and unpractical standards to compile documents that no-one reads (apart from the auditor).

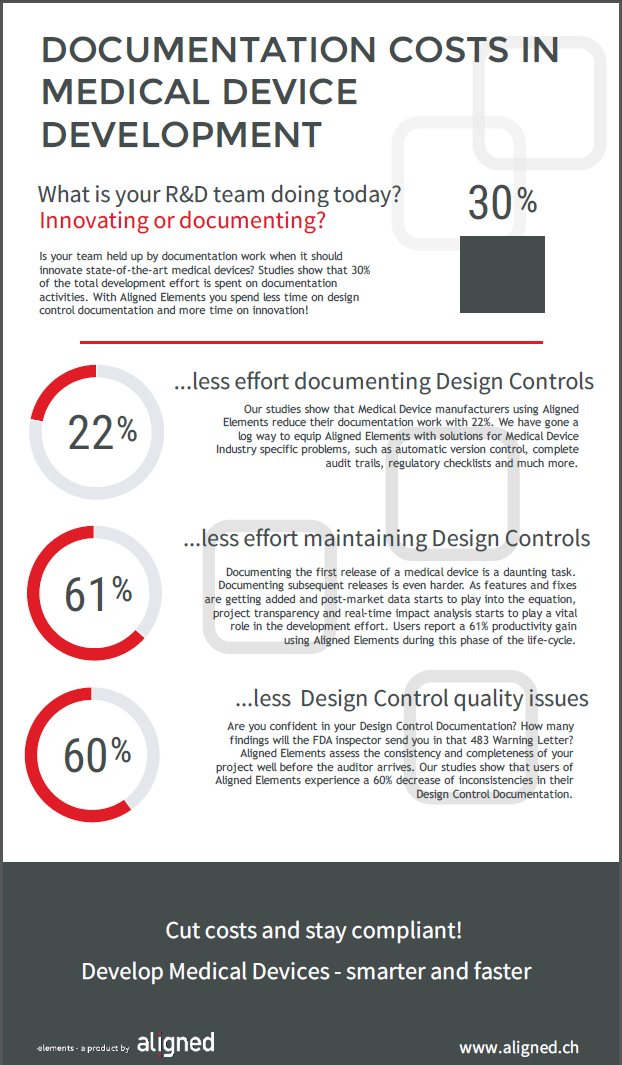
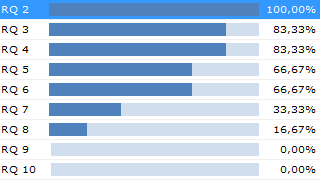
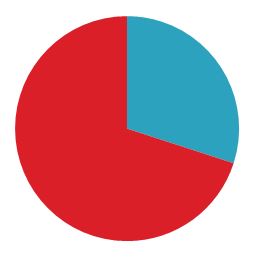
Our studies show that up to 30% of the total project effort is spent on documentation required by regulations. There is also an overwhelming consensus in the industry that this is far too much. Money and time are inefficiently spent and morale buckles as the workload increases.
The good news is that these problems can be fixed. The bad news is that you are going to lose time, money, and people until you fix them.
Excelling at documentation efficiency is not intuitive to many R&D-centric organizations. However, considering the situation described above, good documentation practices is an investment. In the medical device industry, it is even a competitive dimension.
Your company can be efficient!!
Some good starting points are:
- Make documentation efficiency a prioritized objective using measurable goals
- Assign a responsible Manager
- Set up a tight collaboration between the people writing templates and SOPs (Quality people) and the people using the templates and SOPs (R&D people)
- Analyze your documentation processes
- Apply the right software tools to automate documentation tasks
You can start right away!
Download our Medical Device Documentation Self-assessment paper and take a few minutes to complete it. We assure you that you will have started the road to more efficient documentation within the next 15 minutes!